Windows Hacking 1 | TechSecXpert
🔒 TechSecXpert invites you to embark on an enlightening journey into the realm of ethical hacking, focusing on the intricacies of Windows Hacking. In this tutorial, we demystify the techniques, tools, and strategies employed by ethical hackers to secure Windows environments while understanding potential vulnerabilities.
🖥️ Key Insights:
1️⃣ Windows Security Landscape: Gain a comprehensive overview of the Windows operating system’s security architecture. Understand the critical components and potential entry points that ethical hackers explore during assessments.
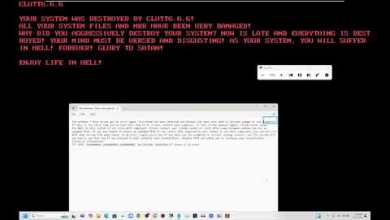
2️⃣ Common Vulnerabilities: Explore common vulnerabilities within Windows systems, from misconfigurations to outdated software. Learn how ethical hackers identify and exploit these vulnerabilities to fortify security measures.
3️⃣ Tools of the Trade: Discover a toolkit of essential tools used in ethical hacking for Windows environments. From privilege escalation to post-exploitation activities, we cover the tools that empower ethical hackers to enhance security.
4️⃣ Hands-on Demonstrations: Join us for hands-on demonstrations as we walk you through practical examples of ethical hacking on Windows. Learn step-by-step techniques and best practices to apply in your own ethical hacking engagements.
💻 Whether you’re an IT professional, cybersecurity enthusiast, or someone curious about ethical hacking, this tutorial equips you with the knowledge and skills needed to navigate and secure Windows environments.
🚀 Don’t forget to like, share, and subscribe for more tutorials on ethical hacking, cybersecurity, and the latest tech trends. Hit the notification bell to stay updated on upcoming videos from TechSecXpert!
🔐 Ready to navigate Windows hacking in ethical hacking scenarios? Subscribe now and become a TechSecXpert! #EthicalHacking #WindowsHacking #TechSecXpert #CybersecurityTutorial #InfoSec
🔐 Empower yourself with knowledge – subscribe now and become a TechSecXpert! 🔐
[ad_2]
source