Malware Analysis – EP 2 | Lab Setup | Malware Hide Tactics
Malware Analysis – EP 2 | Lab Setup | Malware Hide Tactics
Malware Analysis is the process of examining a malicious file or URL to understand its behaviour and purpose. This information can be used to detect and mitigate malware threats, develop new security solutions, and improve the understanding of malware evolution.
Malware Analysis Playlist:
Malware Analysis Part 1:
Malware Analysis Part 2:
Malware Analysis Part 3:
Malware Analysis Part 4:
Malware Analysis Lab Setup
A malware analysis lab is a controlled environment where malware samples can be safely detonated and analyzed. This typically involves using virtual machines (VMs) to isolate the malware from the rest of the network.
Here are some basic steps for setting up a malware analysis lab:
Install a virtualization platform, such as VMware Workstation or VirtualBox.
Create a new VM for each malware sample you want to analyze.
Install a guest operating system on each VM.
Install the necessary malware analysis tools on each VM.
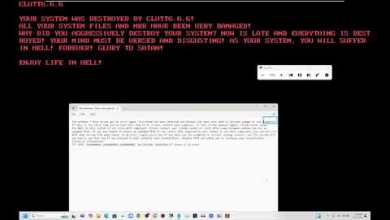
Malware Hide Tactics
Malware authors use a variety of tactics to hide their code and evade detection. Some common tactics include:
Polymorphism: Malware changes its code each time it is executed, making it difficult for signature-based detection systems to identify.
Obfuscation: Malware uses techniques such as encryption, compression, and code scrambling to make its code more difficult to read and analyze.
Rootkits: Rootkits are malware that hides itself and its activity from the operating system. This makes them very difficult to detect and remove.
In this video, I discuss malware analysis in more detail, including how to set up a malware analysis lab and how to identify common malware hide tactics.
malware analysis full course
malware analysis tutorial
malware analysis project
malware analysis tools
malware analysis lab
malware analysis for beginners
malware analysis interview questions and answers
malware analysis sandbox project
malware analysis and reverse engineering
malware analysis using machine learning
What is viruses
What is worms
What is a Trojan horse
What is backdoors
What is botnets
What is ransomware
What is adware
What is APTs
What is zero-day exploits
How to set up a malware analysis lab
malware hide tactics
My Book (Birds Eye View of Cybersecurity):
Linkedin:
Website:
Cybersecurity Interview Question:
#cybersecurity #biswajitsahu #biswajitsahucybersecurity #malwarelabsetup #malwarehidetactics
[ad_2]
source