he hacked my websites
🔥🔥Join the NetworkChuck Academy!:
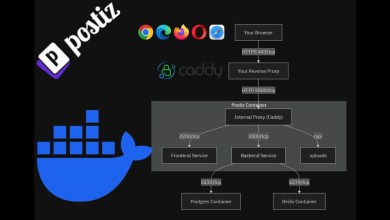
In my last video, I built 24 websites in 24 hours. 🚀 But with such a rapid development sprint, I knew security might have taken a backseat. So in this video, I decided to don my hacker hat and attempt to penetrate my own sites using tools like Nikto, OWASP Zap, Burp Suite, and Snyk. Spoiler alert: I didn’t find much. 😅
Realizing my limitations, I called in reinforcements—my friend and professional ethical hacker Tyler Ramsbey. Tyler took the wheel and performed a thorough penetration test on my websites, uncovering vulnerabilities I had completely overlooked. From exposed API keys to cross-site scripting (XSS) and even accessing hidden admin panels, Tyler shows us how a real hacker would exploit these weaknesses. 😱
Along the way, we discuss how tools like LLMs (Large Language Models) can be both a blessing and a curse in cybersecurity, aiding both defenders and attackers. 🛡️⚔️
Subscribe to Tyler Ramsbey:
SUPPORT NETWORKCHUCK
—————————————————
➡️NetworkChuck membership:
☕☕ COFFEE and MERCH:
Check out my new channel:
🆘🆘NEED HELP?? Join the Discord Server:
STUDY WITH ME on Twitch:
READY TO LEARN??
—————————————————
-Learn Python:
-Get your CCNA:
FOLLOW ME EVERYWHERE
—————————————————
Instagram:
Twitter:
Facebook:
Join the Discord server:
AFFILIATES & REFERRALS
—————————————————
(GEAR I USE…STUFF I RECOMMEND)
My network gear:
Amazon Affiliate Store:
Buy a Raspberry Pi:
Do you want to know how I draw on the screen?? Go to and use code NetworkChuck to get 20% off!!
fast and reliable unifi in the cloud:
Ethical hacking tutorial
Penetration testing your own website
Website security vulnerabilities
How to hack your own site ethically
OWASP Zap tutorial
Using Nikto for server scanning
Burp Suite Pro walkthrough
Exposing API keys risks
Cross-site scripting (XSS) explained
SQL injection prevention
Snyk code analysis tool
Static Application Security Testing (SAST)
Guardio browser security extension
Ethical hacking tools and techniques
Preventing data leaks online
Secure coding practices
Vulnerability scanning with Nuclei
WordPress security flaws
Exposed .git directories dangers
Fixing open redirects
Cybersecurity best practices
Learning ethical hacking with Tyler Ramsby
Securing API endpoints
Protecting your website from hackers
#hacking #cybersecurity
[ad_2]
source


🔥🔥Join the NetworkChuck Academy!: https://ntck.co/NCAcademy
In my last video, I built 24 websites in 24 hours. 🚀 But with such a rapid development sprint, I knew security might have taken a backseat. So in this video, I decided to don my hacker hat and attempt to penetrate my own sites using tools like Nikto, OWASP Zap, Burp Suite, and Snyk. Spoiler alert: I didn't find much. 😅
Realizing my limitations, I called in reinforcements—my friend and professional ethical hacker Tyler Ramsbey. Tyler took the wheel and performed a thorough penetration test on my websites, uncovering vulnerabilities I had completely overlooked. From exposed API keys to cross-site scripting (XSS) and even accessing hidden admin panels, Tyler shows us how a real hacker would exploit these weaknesses. 😱
Along the way, we discuss how tools like LLMs (Large Language Models) can be both a blessing and a curse in cybersecurity, aiding both defenders and attackers. 🛡⚔
Subscribe to Tyler Ramsbey: https://www.youtube.com/@TylerRamsbey
Great video chuck. You have the special sauce when it comes to IT learning videos!
u are my fav bro >3
вывывы
hey can you or anyone help me hack someones channel and delete thay channel on telegram? please i really need your help..
Brother can u help me ….please 🙏
Chuck have you heard about the Red Hat Enterprise Linux Ai? I am reading about it in a PDF I found on Red Hats website today, the document was posted on the 18th September, 24.
This was the very first time i saw a hacker doing his job with his know how!
How exhausting this kind of thing can be for someone.
Karma attacks can be done with a wan and Kali Linux using Aircrack-ng. But you do not have consent, unless you do.
And have ISO Policies like Business Continuity.
I learned what "sanitizing user input" meant when I tried to figure out why a now defunct social media site that for some reason allowed HTML in posts would change "Runescape" into Rnotallowed". It was "sanitizing" some javascript.
That led me into breaking forms and making buttons do different things on the page. Like instead of deleting my vulgar comment, it deleted a group of 30k+ people.
Teenager me was annoying. And maybe a little criminal. Just ask those old guys that thought I was 12, and female, and needed prepaid cell phone minutes. And then my account logged out and they never saw me again. I was 14, and male. And I did in fact need prepaid cell phone minutes, but not to call them.
Hey Chuck can you make a video on how to find secrets on people like hack in their phones and discover secrets don't worry i just want to learn how because I want to become a ethical hacker
I did a full-blown pen test on a company I consult for. The admins were so pissed at me after I found over 256 vulnerabilities in their system. They were claiming there wasn't any and were adamant that I was wasting my time. Granted some where minor ones but there was some really bad ones. That opened up to get their data stolen. I love doing these especially with self-entitled admins who think they are better than everyone. 🤣🤣
He can do all that but never stuck his finger in a hole made by nature 😂
at 19:24 before he connects to the VPN he shows his real IP
root rogin
Cool!
3:01 they should make it so you have to verify domain ownership first.
I have seen all videos of this Chuck Guy but he wont teach you anything at all. this Channel is not useful ,
I am currently studying for CCNA and I want to know which platform would be better for practice exams. Boson or Alphaprep. Need suggestions 🙂
How to show hidden networks in Kali Linux
Can you help me set up my Alfa adapter in Linux so I can start testing?
saying yourself noob at cybersecurity is calling newbies trast at cybersecurity 🤣
Need more videos like this please ❤
Don't hack meeeee i know you want to!!!!!!!!!!!!
Hello @NetworkChunk! I been watching your videos for 5+ years. Can you make a video about armitage as an favor. [Like this comment if u accept]
☺
I subscribed this channel for hacking content, Now I know More about coffee than hacking.🤣
I think he is slowly becoming James Hoffman 😂
17:05 "GoWitness? I've never heard of this!"
17:30 "GoWitness is cool. I've heard of it but never used it before."
It's so small and kinda silly but for some reason this made me lose some trust and made me sad.
fun enough I came from tyler's channel love this colab
Chuck, you saying you are not allowed to hack me I really don’t like because it makes it sound like you’re saying I can’t access the information you have that is Public but do understand private information
Chuck, please put some of you applications behind Cloud flare and re-test.
I waited him to hack into the linode server but he didn't !
zaproxy is NOT installed by default. but ok
No I’m not Human, I’m Peter ❤
This is exactly why hacking is no more a powerful source ..when you have ppl creating script kiddies online.
how disappointing.. pinapple on pizza
Great video though!
Guessing those sites were on a hostinger shared host. You didn't violate tos or anything for their shared hosting running pen tests like this with nuclei?
You are pretty lame script kiddo, im not suprised at all 🙃🤣
Hi, NetworkChuck can you please help me recover my IG account? Someone got hacked my account 😭 Please…
pls i want to ask, how/where do i get an api of a website?? pls @NetworkChuck reply
Glen Bypass
Gritty coffee? Perhaps there's something wrong with your french press?
Yooooo my favorite rapper is here
ruh roh! root rogin!
9:25 Yes it is important to sanitize the data that the user sends into your webpage.
No one knows why this comment got so much attention and so many like and dislikes